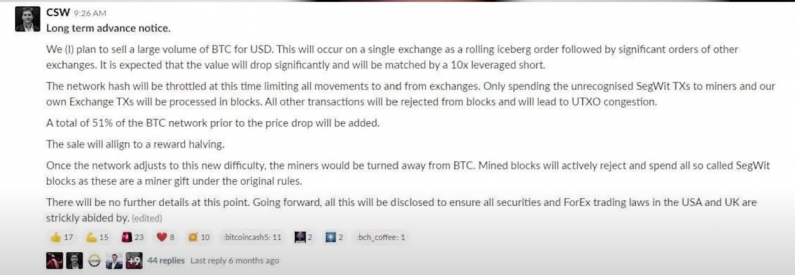
“The 51% Attack
The 51% attack is a method of using large amounts of hashrate to generate fraudulent transactions, by spending the same coin twice, thus having one of the transactions canceled and defrauding the recipient. In essence, if a miner who controls a large percentage of the hashrate manages to solve proof‐of‐work problems quickly, he could spend a bitcoin on a public chain that receives confirmations while mining another fork of the blockchain with another transaction of the same bitcoin to another address, belonging to the attacker. The recipient of the first transaction receives confirmations, but the attacker will attempt to use his processing power to make the second chain longer. If he succeeds in making the second chain longer than the first one, the attack succeeds, and the recipient of the first transaction will find the coins they received vanish.
The more hashrate the attacker is able to command, the more likely he is to make the fraudulent chain longer than the public one, and then reverse his transaction and profit. While this may sound simple in principle, in “practice it has been much harder. The longer the recipient waits for confirmation, the less likely it is that the attacker can succeed. If the recipient is willing to wait for six confirmations, the probability of an attack succeeding shrinks infinitely low.
In theory, the 51% percent attack is very feasible technically. But in practice, the economic incentives are heavily aligned against it. A miner who successfully executes a 51% attack would severely undermine the economic incentives for anyone to use Bitcoin, and with that the demand for Bitcoin tokens. As Bitcoin mining has grown to become a heavily capital‐intensive industry with large investments dedicated to producing coins, miners have grown to have a vested long‐term interest in the integrity of the network, as the value of their rewards depends on it. There have been no successful double‐spend attacks on any Bitcoin transactions that have been confirmed at least once.
The closest thing to a successful double‐spend attack that Bitcoin has witnessed was in 2013, when a Bitcoin betting site called Betcoin Dice had a sum in the range of 1,000 bitcoins (valued at around $100,000 at the time) stolen from it through double‐spend “attacks utilizing significant mining resources. That attack, however, only succeeded because Betcoin Dice was accepting transactions with zero confirmations, making the cost of attack relatively low. Had they accepted transactions with one confirmation, it would have been much harder to pull off the attack. This is another reason Bitcoin's blockchain is not ideal for mass consumer payments: it takes somewhere in the range of 1 to 12 minutes for a new block to be generated to produce one confirmation for a transaction. Should a large payment processor want to accept taking the risk of approving payments with zero confirmations, it constitutes a lucrative target for coordinated double‐spend attacks that utilize heavy mining resources.
In conclusion, a 51% attack is theoretically possible to execute if the recipients of the payment are not waiting for a few blocks to confirm the validity of the transaction. In practice, however, the economic incentives are heavily against owners of hashpower utilizing their investments in this avenue, and as a result, there have been no successful 51% attacks on node members that have waited for at least one confirmation.”